Tech specs & Security
Software as a service – Personal data protection – Security – GDPR compliance
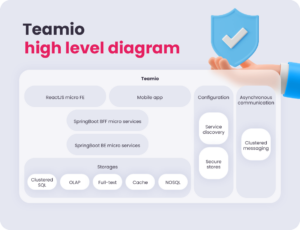
Teamio is a fully modular, multi-tenant web-based applicant tracking system with a mobile app.
It facilitates effective info sharing between companies and job seekers. It helps to maintain a recruitment process across the whole company, looking for candidates who fit requirements, posting job openings, keeping communication history with relevant job candidates, managing job tenders and interviews with team leaders And much more. All, of course, in compliance with EU legislation. It’s secure. Effective. Convenient. It’s Teamio.
Software as a Service
Teamio is run as a SaaS (Software as a Service), which simply means:
- it is operated in a private cloud
- it is located at multiple data centers to ensure high availability
- Teamio’s cloud solution is hosted in the AWS Europe (Ireland) Region (eu-west-1)
- Alma Career as the Application Service Provider (ASP) ensures continuous operation
Personal Data Protection
Access Restrictions
- User data can be accessed only by a restricted group of authorized staff.
- Concerning sensitive data, security measures always include full tracking of operations and activities associated with the operator identity.
Role Segregation
We recognize the following roles from the very nature of user request handling:
- CustomerCare [40+] – receives customer requirements and try to process (in the first-line)
- Support [20+] – technical support staff (second-line of processing pipeline)
- Business [20+] – solves functional requirements for products, campaigns, etc. (3rd line)
- System administration [10+] – maintains tech resources (servers, backups…)
The roles described above have to (or potentially may) have access to part/complete user data. Indicative staffing numbers may help to depict the size of support inevitably accessing sensitive data.
Personal Data Deletion
There are two ways to delete the personal data of a candidate:
1) Manual deletion
There is an option to delete candidates (all editions). Two means of deleting candidates are accessible via the Candidate Search or in the Candidate Card.
The deleted candidate will disappear from all views, including history, notes, labels, and so on. It is an irreversible step. The candidate is deleted from our database too, and so disappears from all linked positions as well.
2) Automatic deletion
- Teamio Mini edition – All candidates are automatically deleted after archiving the position.
- Teamio Professional, Teamio Enterprise, Teamio Solo, Teamio Essential – The candidates are deleted only if the candidate did not give consent for the processing of related personal data (6 months after their first contact) or after the candidate’s consent has expired (if the candidate previously granted it to the employer). Otherwise every contact remains in the client’s Teamio database as long as the consent is valid.
Each client can choose an individual period of validity of consent.
Deletion of personal data is always an irreversible step.
Recovery of deleted candidates is not possible due to all related data being permanently anonymized.
There is no way beyond this point to gather any info (including the majority of auditing info) about a deleted candidate or any related activities.
The one and only exception to this is the Consent log (see Audit section below).
Technical Security Measures
- User access is provided solely by encrypted connection
- We use two-factor verification for user login
- The non-production (development / testing) environment is separated from production-grade data
- User data is confined within production, non-production uses a synthetic/obfuscated data corpus
- Security-relevant activities on production systems are monitored, logged and time-evaluated
- The activation of components/services (per user request) is always validated on the Alma Career side
- The Teamio solution is continuously being developed and tested (functionality and security together)
- Updates and patches are released on a daily basis (or sooner in the case of serious trouble)
User Support
Support requests are collected and registered using Liveagent and Intercom and processed by Customer Care team in the shortest possible time, during standard business hours (Mon-Fri, 08-17 CET, Prague).
Contacts:
- pomuzeme@teamio.com (CZ, EN)
- pomozeme@teamio.com (SK, EN)
- pomoc@teamio.com (PL, EN)
- Tel.: +420 224 810 055 (CZ, EN)
- Tel. +421 2 33 00 67 91 (SK, EN)
Compatibility & Minimum Requirements
- Teamio is accessible through a web browser (it is compatible with major browsers – Firefox, Chrome, Explorer/Edge, Safari at least)
- Support of JavaScript and cookies is required
- Google Chrome is recommended by our team
Security
Data in Transit
Web access allows HTTPS (encrypted) connections only.
- TLS 1.2 protocol is enforced
- The X509v3 SSL certificate is signed by trusted CAs (accepted by all major web browsers)
- A client certificate is not required
Separation of individual client sessions is ensured by the cookies mechanism.
All production system traffic in both directions is filtered and only HTTPS for user interaction and encrypted access (SSH protocol with key authentication) for maintenance / updating of the application is enabled.
Authentication
User verification (Sign-in) involves a double-factor, form-based (user/password) mechanism with a code sent to the user’s contact e-mail address (or other option) for double approval.
User accounts are treated as individual (Alma Career strongly discourages sharing accounts among multiple users).
The number of attempts to log in to the system using a particular user identity is dynamically restricted to protect against brute-force password attacks. The plain text password is never stored and is present only in-memory at the time of user login. Passwords are stored only hashed. The hashing algorithm is continually modified to respond to the changing state of technology.
Login parameters must meet the password policy. The current settings are as follows:
- The username is a unique identifier (an e-mail address can also be used).
- The minimum enforced password length is 8 characters, maximum is limited to 128 characters.
- Password complexity is enforced (a combination of at least two character sets of digits, characters, special characters).
- So-called trivial passwords (numeric / character series, e.g. 123456, abcdef) are rejected.
- The initial password (after setting up the user / password setting by the operator) must be changed at the next login.
- The password change is not enforced (i.e. the password does not expire), therefore the history of used passwords is not recorded.
- The password-hashing algorithm is PBKDF2(HMAC-SHA256), 1M iterations, and ”salted“ individually per account.
- 5 unsuccessful attempts at logging in blocks the particular user account for one hour.
Authorization (User roles)
Each Teamio user has a defined role, which results in a unique set of permissions and access to various functions and parts of Teamio for the given client. A new user can be invited to the client’s account by a colleague who has permission to onboard new users and assign them permissions. They can either choose from predefined roles or create a unique role.
The following user roles are defined (availability depends on Teamio edition):
- HR Manager – has access to all registered job openings & to all responses to these postings. They may change company profile settings (templates, headers, etc.). Can be (optionally) set to any combination of the following rights
- Access to service statistics
- Access to recruitment statistics
- Access to account credit administration
- User account management
- Recruiter – has access only to their own registered job openings & relevant responses. There is no right to change company profile settings. This role has the following privileges:
- Access to the shared pool of candidates,, including access to those of other recruiters(within the tenant) who have been pre-selected, interviewed, or joined.
- Access to incoming messages (if the edition contains the Inbox service).
- Recruiter (without the possibility of spending credits) – differs only in blocking credits (e.g. payment by credit for posting, unhiding a CV in the database, etc.)
- Line Manager – has access only to the candidates for job openings shared with them. There is no right to change company profile settings or work with a job posting. This role can:
- Add comments
- Invite candidates to interviews
A custom role can have unique access and permissions according to user and company preferences.
Data at Rest
Teamio code runs sandboxed on WildFly application servers built-up on top of hardened Linux operating systems.
All components run virtualized on AWS cloud to ensure high-availability and fast disaster recovery options. All sensitive data is encrypted “at rest” using AES-256 encryption.
The main portion of data is kept within a High Availability Disaster Recovery database back-end (PostgreSQL).
Data is continuously synchronized and mirrored to multiple locations, and backups are also made on a regular basis.
Backups take place according to a defined plan (retention is implicitly set for 14 days):
- All servers are backed up by the cloud provider in the form of a volume snapshot
- The transaction log backup is ongoing (to ensure data recovery within one working day of the crash)
- The snapshot of the cloud platform takes place daily, every 4 hours
- A full data backup data runs weekly
A multi-level backup system is used:
- Online replication of data to multiple locations
- Backup of the private cloud itself
- Internal backup systems
Monitoring & Supervision
Operations monitoring runs continuously (24×7).
The status is supervised (and any issues notified) daily (07-22 CET):
- external monitoring services together with internal systems are employed to check the status
- to check the three-month uptime history of the core Teamio entry points, visit http://stats.pingdom.com/xxltcf7m2rk7
Development Cycle
The development, integration and testing environments are fully virtualized and run on a private cloud platform. The environments are logically split (by firewalling). Access rights to the individual environments are different. To reiterate, the production environment is fully separated (physically) from non-production environments.
Planning, development and testing of any updates/new releases of Teamio takes place in the framework of agile development (We cycle using SCRUM Sprints).
All used components (including those developed in-house) are tested for stability, availability, and security prior to production deployment, so that vendor / platform manufacturer support is always maintained.
In the case of identified security flaws, updates (patches/fixes) are applied after testing in the shortest possible time.
Testing takes place in a continuous and multi-level development regime:
- Prior to accepting any change in the source code, a developers’ review (local Lint and four-eye control principle) takes place.
- In the framework of code quality control, static code analysis is performed (using code review instruments).
- The application is further checked (still pre-production) by dynamic analysis (using specialized penetration test tools).
- Regular (annual) independent assessment of application security (through penetration testing) is also carried out by specialized 3rd parties.
Passing tests begins the release management process to move the new code to production. This is a fully automated (no manual intervention allowed) deployment process with full audit tracking (to ensure rollback to the last good version, should deployment fail).
Auditing
Audit records are made to track all significant activities of users. Audit (logging) is layered, descending from the application level to the system as follows:
- History (of user activities)
- Business log
- GDPR log
- Security log
- Application log
- System log
- Consent log
Each record is tied to a timestamp and user identity. Records are kept in the log(s) for the period specified for a particular audit track, but at least 180 days.
History
Detailed info about user activities (e.g. reasons for refusal, “brand” from which the response was delivered, etc.), currently comes from the modules:
- Candidate Activities
You can click on the Candidates/Detail anywhere in the Candidate List. The response history is also shown here, as it relates to the specific recruitment campaign you are viewing. If you wish to see the entire history of the candidate in Teamio in the Response Detail, click on the link All History. - Recruitment Activity
In the list of active positions, click on the position name to get Recruitment Details (a brand new view). Here you can find the most important information about the entire recruitment campaign and activity logs related to job postings, specifically in the Job Posting History section. - Activities above company (tenant) users
Upon request we provide an additional log of activities (not included in your space). It relates to user’s management within your registration. We keep the log for 5 months. It includes:- Transfer of admin privileges
- Change of user status
- Change of company login name
Business log
Detailed info about particular user actions/automated system actions (over 700 different types of event are currently registered – operations with positions, candidates, service orders, etc.).
Security log
Info about security-related actions (e.g. verification result etc.).
System log
Low-level application events:
- HTTP requests
- Database access
- Performance measurement info
- Application errors
Consent log (GDPR related)
We keep the information in the consent log for ten years.
It includes:
- Name, Surname, E-mail address of the candidate
- Business ID
- The date of the consent / the non-consent
- Referral
Check the GDPR compliance section for more detailed info.
Security Assurance
All the main principles, measures and technical solutions used to safely develop and operate Teamio and protect sensitive user data are listed on this page.
Upon request, we provide our business partners with a detailed description of Alma Career security measures in the format defined by the ISO/IEC 27001.
This level of providing security information to third parties is final (no further security info, like Test Reports, Internal Security Guidelines etc. are provided outside Alma Career).
Declaration of Conformity
We confirm that the web service provided by us is developed in accordance with the current knowledge of application security.
As part of the risk management process, we periodically identify risks to our services caused by potential vulnerabilities and implement measures to suppress them.
The service is regularly subjected to security audits according to the OWASP ASVS Level 3 criteria (OWASP Application Security Verification Standard) in order to guarantee the resistance of the service to known vulnerabilities, regularly defined in the OWASP Top 10 ranking.
The severity of vulnerabilities is evaluated according to the CVSS Base Metric Group methodology, and according to our criteria, production services must not contain vulnerabilities higher than Low (on the None-Low-Medium-High-Critical scale).
As a matter of principle, we do not provide other materials or greater detail regarding our security measures.
GDPR compliance
Processing and protection of user data is ensured in accordance with EU legislation (GDPR).
All detected breaches of sensitive (personal) data protection are reported to both the supervisory authority and the data subject within the reporting obligation (according to GDPR).
The scope and content of the report is precisely specified by legislation (EU Regulation 2016/679, Articles 33, 34), which we strictly follow.
The full text of the GDPR directive is available on the European Commission official site.
Teamio / Alma Career process the personal information of candidates who respond to job openings. The data controllers for this information are, however, the employers who publish job opening postings.
The Data Processor
Our responsibility is to process candidates’ personal data for clients (Data Controllers).
Teamio / Alma Career are responsible for:
- Managing the platform that enables the processing of candidates’ data.
- We process this data based on your instructions and in line with a contract with you as its data controller.
- We take into account the nature of candidate-data processing by utilizing suitable technical and organizational measures to ensure that our data processing complies with GDPR requirements and ensures the protection of candidates’ rights.
- We ensure that, on the processor’s side, candidate data is processed solely by persons bound by a non-disclosure agreement.
- We provide the cooperation needed to ensure the adequate processing of personal data by the data controller.
Data Controller
i.e. the employer who collects information on candidates during a recruitment campaign.
The data controller is responsible for ensuring that:
- Adequate technical and organizational measures are implemented to make it easy to prove that your data processing is GDPR-compliant.
- You process only such personal information as is necessary for the given, predefined, specific purpose (for example, the recruitment process).
- When two companies share a registration in Teamio, these two companies are considered joint controllers in terms of GDPR. They must decide between themselves which of them is responsible for which part of data processing, especially in connection with the exercising of data subjects’ rights.
Data Subjects
The candidates are the “data subjects” because we can (in)directly identify them using their personal information.
Personal information
Information connected with a data subject. This might be their name, e-mail address, telephone number, CV, notes, labels, or recorded actions.
Data Processing
Actions performed on personal information by the data controller or processor; these are fully or partly automated (collection, recording, organizing, storing, and deleting).
There are two separate personal data processing regimes
- Processing of personal data based on a purpose, in this case a response to a job opening. This purpose is valid for a maximum period of 6 months. During this period, you can include the candidate in the selection procedure for the job opening they applied for or offer them another relevant job. We will also let the candidates know how their data is to be processed for you. Our lawyers have already approved the wording of the notice that will be included in the job postings.
- Processing of personal data based on a voluntary consent, beyond the scope of processing for recruitment purposes. This will allow you to process the personal data of your candidates for 3 years. The new consent forms have already been polished by our lawyers and we are now testing them directly with candidates.
How long can you keep a candidate in Teamio?
The amount of time is always limited.
A candidate who has not provided you with voluntary consent can stay in the Teamio database for a maximum period of 6 months. They will then be automatically deleted after the job posting has been archived, or after 6 months have passed.
A candidate who has provided you with voluntary consent (beyond the scope of the recruitment process) can stay in your database for up to 3 years.
Plus, you will always know when a candidate’s consent to the processing of personal data is about to expire – we will notify you 2 months in advance.
Data Protection Officer
Didn’t find an answer to your question regarding GDPR? Ask our specialist on personal data protection:
Ján Jaroš: DPO-CZ@almacareer.com
Ready to take your recruiting to the next level?
Let’s make a call. We’ll show you how to reach higher goals with Teamio. Try Teamio for 30 days for free.
